Digital identity:AccessMatrix introduction
DIGITAL IDENTITY:Platform introduction
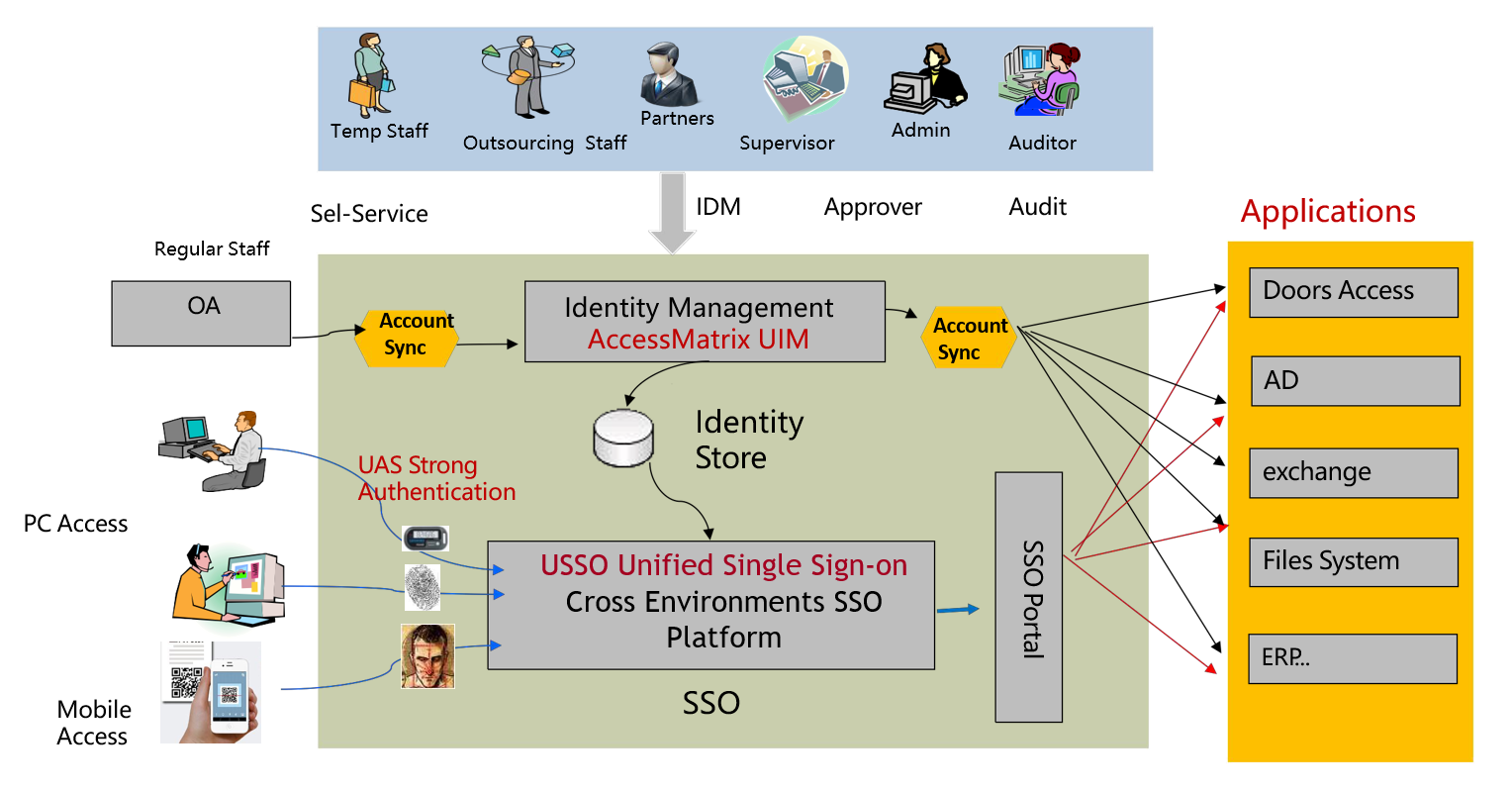
Identity and Access Management, Versatile Authentication and SSO Platform
Universal identity management platform (UIM): automatically add, delete, modify and check user accounts, and realize full life cycle management for all types of user accounts
Universal authentication platform (UAS): realize two factor authentication and improve the login security of business system
Universal single sign on (USO): use AI password memory mode to log in to the business system uniformly without interface modification
Universal access management (UAM): use the interface transformation method to uniformly log in to the business system and improve the user experience
Universal voucher management (UCM): manage the IT infrastructure operation and maintenance account throughout its life cycle
Integrated Business Model
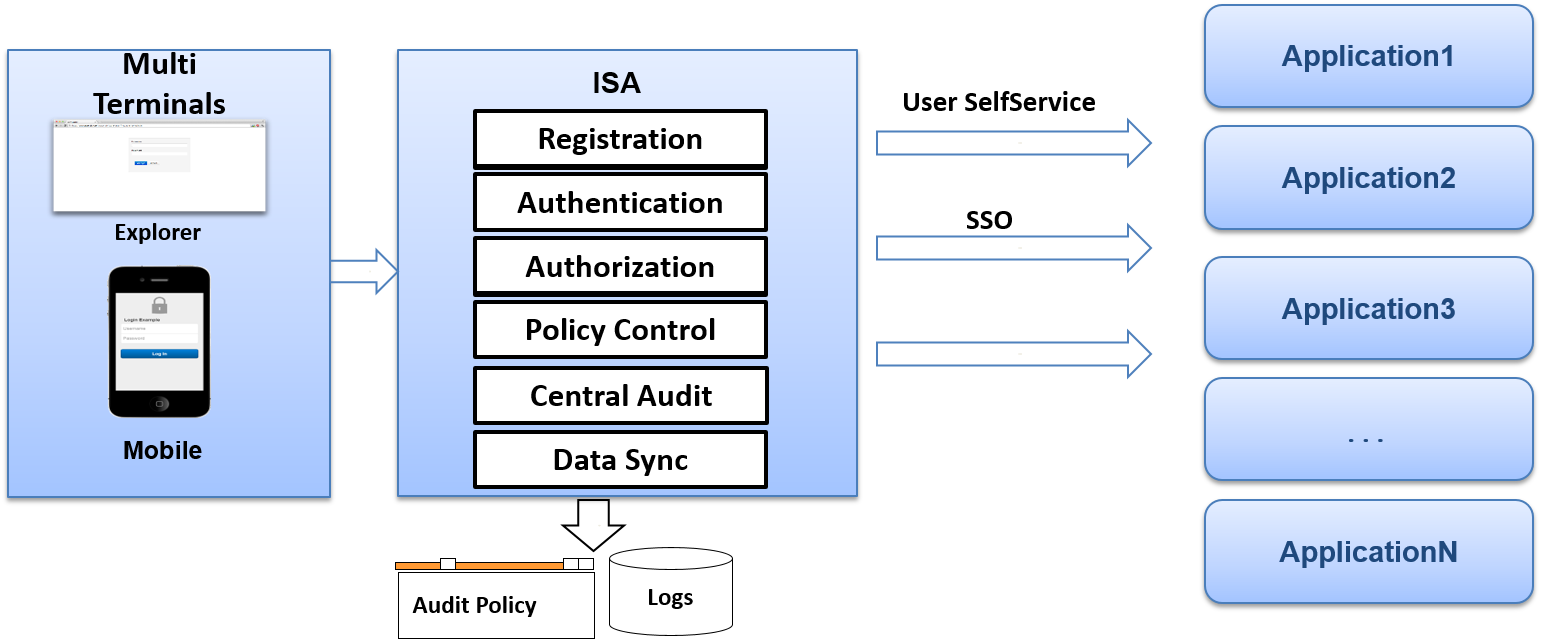
AccessMatrix™ ISA provides common security services to provide centeral management for all applications. It provide many ways to help customer to integrate various applications via one common security platform. It can simply operations , reduce the cost with best service.
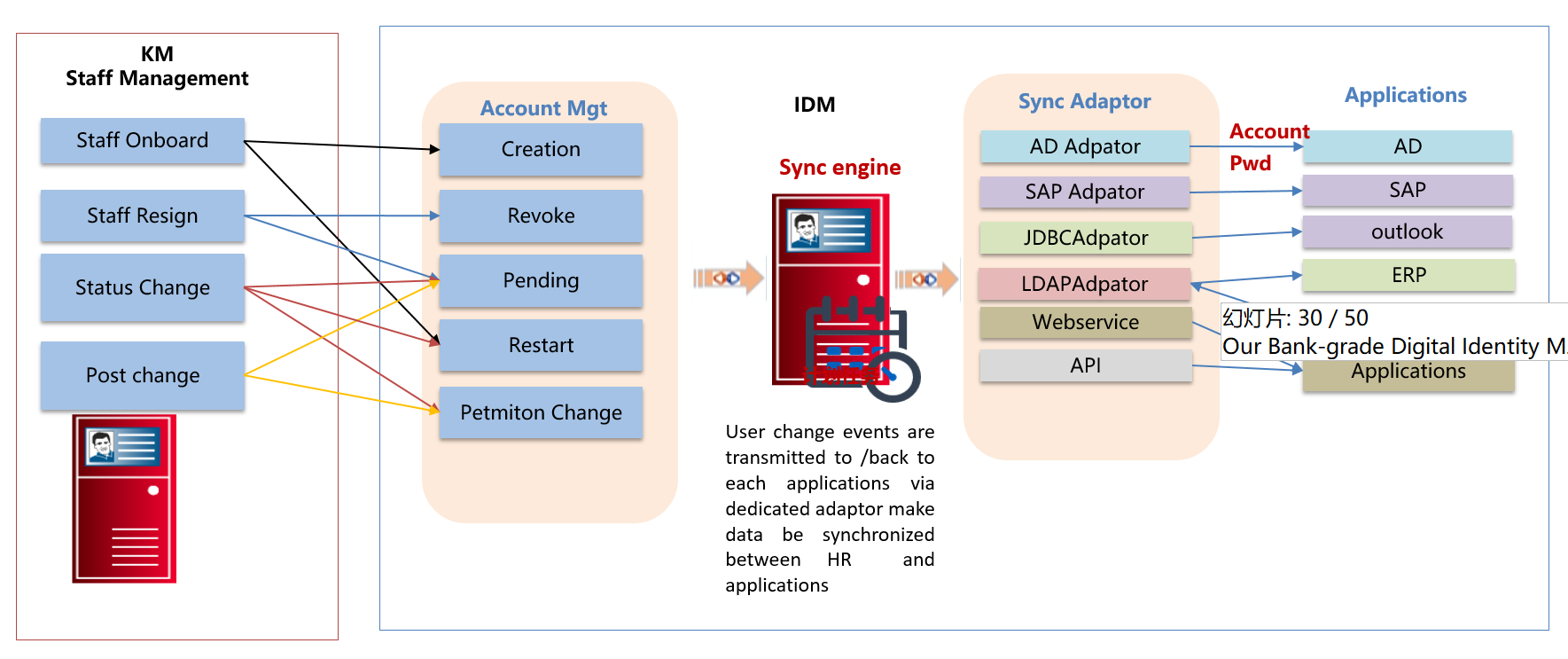
Identidy Life cycle management will create a master identity store via way of "dispersing to centralize" . It will unifies the user account and password info originally dispersed in each applications to the master store and will be managed centrally. It will provide user identity info for all application atuomatically. database for information systems. It will be an unified user identity standards for applications.